In the
Hacking Windows 95, part 1 blog post, we covered that through a nasty bug affecting Windows 95/98/ME, the share password can be guessed in no time. In this article, I'm going to try to use this vulnerability to achieve remote code execution (with the help of publicly available tools only).
The first thing we can do when we have read access to the Windows directory through the share, is to locate all the *.pwl files on the c:\windows directory, copy them to your machine where Cain is installed, switch to Cracker tab, pwl files, load the pwl file, add username based on the filename, and try to crack it. If you can't crack it you might still try to add a .pwl file where you already know the password in the remote windows directory. Although this is a fun post-exploitation task, but still, no remote code execution. These passwords are useless without physical access.
One might think that after having a share password and user password, it is easy to achieve remote code execution. The problem is:
- there is no "at" command (available since Windows 95 plus!)
- there is no admin share
- there is no RPC
- there is no named pipes
- there is no remote registry
- there is no remote service management
If you think about security best practices, disabling unnecessary services is always the first task you should do. Because Windows 95 lacks all of these services, it is pretty much secure!
During my quest for a tool to hack Windows 95, I came across some pretty cool stuff:
LanSpyBut the best of the best is
Fluxay, which has been written by chinese hackers. It is the metasploit from the year 2000. A screenshot is worth more than a 1000 words. 4 screenshot > 4 thousand words :)
It is pretty hard to find the installer, but it is still out there!
But at the end, no remote code execution for me.
My idea here was that if I can find a file which executes regularly (on a scheduled basis), I can change that executable to my backdoor and I'm done. Although there is no scheduler in the default Windows 95, I gave it a try.
Let's fire up taskman.exe to get an idea what processes are running:
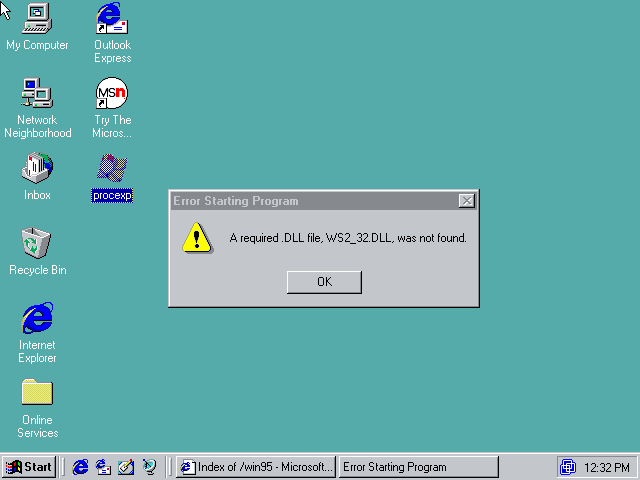
Looks like we need a more powerful tool here, namely Process Explorer. Let's try to download this from oldapps.com:
LOL, IE3 hangs, can't render the page. Copying files to the Win95 VM is not that simple, because there are no shared folders in Win95 VM. And you can't use pendrives either, Win95 can't handle USB (at least the retail version). After downloading the application with a newer browser from oldapps, let's start Process Explorer on the test Windows 95.
Don't try to download the Winsocks 2 patch from the official MS site, it is not there anymore, but you can download it from
other sites.
Now let's look at the processes running:
After staring it for minutes, turned out it is constant, no new processes appeared.
Looking at the next screenshot, one can notice this OS was not running a lot of background processes ...
My current Win7 has 1181 threads and 84 processes running, no wonder it is slow as hell :)
We have at least the following options:
- You are lucky and not the plain Windows 95 is installed, but Windows 95 Plus! The main difference here is that Windows 95 Plus! has built-in scheduler, especially the "at" command. Just overwrite a file which is scheduled to execution, and wait. Mission accomplished!
- Ping of death - you can crash the machine (no BSOD, just crash) with long (over 65535 bytes) ICMP ping commands, and wait for someone to reboot it. Just don't forget to put your backdoor on the share and add it to autoexec.bat before crashing it.
- If your target is a plain Windows 95, I believe you are out of luck. No at command, no named pipes, no admin share, nothing. Meybe you can try to fuzz port 137 138 139, and write an exploit for those. Might be even Ping of Death is exploitable?
Let's do the first option, and hack Windows 95 plus!
Look at the cool features we have by installing Win95 Plus!
Cool new boot splash screen!
But our main interest is the new, scheduled tasks!
Now we can replace diskalm.exe with our backdoor executable, and wait maximum one hour to be scheduled.
Instead of a boring text based tutorial, I created a YouTube video for you. Based on the feedbacks on my previous tutorialz, it turned out I'm way too old, and can't do interesting tutorials. That's why I analyzed the cool skiddie videoz, and found that I have to do the followings so my vidz won't suck anymore:
- use cool black windows theme
- put meaningless performance monitor gadgets on the sidebar
- use a cool background, something related with hacking and skullz
- do as many opsec fails as possible
- instead of captions, use notepad with spelling errorz
- there is only one rule of metal: Play it fuckin' loud!!!!
Related word
- Pentest Recon Tools
- Hacking Tools Name
- Hack Tools Mac
- Best Hacking Tools 2019
- Hack Tools Github
- Hacking Tools Usb
- Pentest Tools For Ubuntu
- Pentest Tools Free
- Kik Hack Tools
- Hacking Tools Name
- Hacking Apps
- Ethical Hacker Tools
- Hacker Tools For Pc
- Hacker Tools Windows
- Hacking Tools For Mac
- Hak5 Tools
- Hacks And Tools
- Hacker Tools Mac
- Hak5 Tools
- Pentest Tools Online
- Beginner Hacker Tools
- Pentest Tools Kali Linux
- Beginner Hacker Tools
- Hacking Tools Usb
- Pentest Tools For Android
- Hacker
- Hacker Tools Online
- Hacking Tools And Software
- Hacker Search Tools
- Pentest Tools Kali Linux
- Hack Tools For Windows
- How To Hack
- Ethical Hacker Tools
- New Hack Tools
- Pentest Tools Framework
- Hack Tools 2019
- Hacking Tools Free Download
- Pentest Recon Tools
- Hackrf Tools
- Kik Hack Tools
- Best Hacking Tools 2019
- Best Hacking Tools 2019
- Physical Pentest Tools
- What Is Hacking Tools
- Hacker Tools Apk
- Hak5 Tools
- Hacking Tools Download
- Hacker Tools Github
- Nsa Hack Tools
- Hacker Tools Mac
- Hackrf Tools
- Pentest Tools Android
- Hacking Tools For Windows
- Android Hack Tools Github
- Hacker Tools 2020
- Pentest Tools Linux
- Blackhat Hacker Tools
- Pentest Tools
- Hack Tools For Windows
- Easy Hack Tools
- Hacker Tools Free Download
- Beginner Hacker Tools
- Underground Hacker Sites
- Hacker Tools Online
- Pentest Automation Tools
- Hack And Tools
- Easy Hack Tools
- Hacking Tools Free Download
- Pentest Tools List
- Hacking Tools For Games
- Pentest Tools Bluekeep
- What Are Hacking Tools
- Hacking Tools Windows
- Computer Hacker
- Hacking Tools Pc
- Hackrf Tools
- Free Pentest Tools For Windows
- Hacker Tools Linux
- Hack Tools 2019
- Hacker Tools Apk
- Free Pentest Tools For Windows
- Hacking Tools And Software
- Hacker Tools Mac
- Hacker Tools Hardware
- Hack Tools Online
- Pentest Tools Online
- Hacker Tools Software
- Hacker Tools Free
- Pentest Recon Tools
- Hacking Tools Usb
- What Are Hacking Tools
- Pentest Tools Github
- Pentest Tools Tcp Port Scanner
- Pentest Tools Website Vulnerability
- Hacking Tools Download
- Hacker Tools Mac
- Hacker Techniques Tools And Incident Handling
- Hacking Tools Software
- Pentest Tools Url Fuzzer
- Hack Tools 2019
- Pentest Tools Port Scanner
- Computer Hacker
- Pentest Tools Url Fuzzer
- Hacking Tools For Beginners
- Hacking Tools 2020
- Pentest Automation Tools
- How To Make Hacking Tools
- Pentest Tools Framework
- Pentest Tools Kali Linux
- Pentest Tools Free
- Hacking Tools Windows 10
- Hacking Tools For Mac
- Hacking Tools For Pc
- Hack Tools Github
- Hacking Tools Mac
- Pentest Tools Github
- Hack Tool Apk No Root
- Black Hat Hacker Tools
- Hacker Tools Apk
- Pentest Box Tools Download
- How To Hack
- Pentest Tools Download
- Usb Pentest Tools
- Nsa Hack Tools
- New Hack Tools
- Hacker Tools Github
- Pentest Tools For Android
- Hacking Tools For Kali Linux
- Hacking Tools
- Pentest Tools For Windows
- Hack Tool Apk No Root
- Pentest Tools For Android
- Pentest Tools Alternative
- Pentest Tools Tcp Port Scanner
- Hackers Toolbox
- Hack App
- Hacking Apps
- Hack Tool Apk
- Pentest Tools Kali Linux
- Pentest Tools Open Source
- Hacking App